Hi,
Not sure where to post this (B4J or B4i forum) so I posted it here, as I am not sure what end is causing my issue.
I am using MQTT to send data from my B4J app (non-UI) to my B4i app.
Sending the text to the topic in plain text and receiving it in B4i works fine.
Soon as I encrypt the message it is causing an issue.
I am using the following code..
B4J:
B4i:
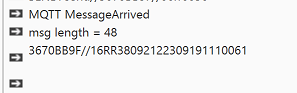
For some reason, it is adding extra characters to the end of the message from what I can see.
Like I said, when I send it as plain text without encrypting the message it works fine.
Any ideas on what I have done wrong ?
Not sure where to post this (B4J or B4i forum) so I posted it here, as I am not sure what end is causing my issue.
I am using MQTT to send data from my B4J app (non-UI) to my B4i app.
Sending the text to the topic in plain text and receiving it in B4i works fine.
Soon as I encrypt the message it is causing an issue.
I am using the following code..
B4J:
B4X:
Type MQTTMSG (message As String)
' sending MQTT message
MqttClient.Publish2("test", CreateMessage(msg), 0,False)
Public Sub EncryptText(text As String) As String
Dim c As B4XCipher
Return su.EncodeBase64(c.Encrypt(text.GetBytes("utf8"), "SecurePassword"))
End Sub
public Sub CreateMessage(msg As String) As Byte()
Dim m As MQTTMSG
m.Initialize
m.message = EncryptText(msg)
Return serializator.ConvertObjectToBytes(m)
End SubB4i:
B4X:
Type MQTTMSG (message As String)
Public Sub DecryptText(EncryptedData As String) As String
Dim c As Cipher 'iEncryption Lib
Private su As StringUtils
Dim b() As Byte = c.Decrypt(su.DecodeBase64(EncryptedData), "SecurePassword")
Return BytesToString(b, 0, b.Length, "utf8")
End Sub
Private Sub MqttClient_MessageArrived (Topic As String, Payload() As Byte)
Log("MQTT MessageArrived")
Dim receivedObject As Object = serializator.ConvertBytesToObject(Payload)
Dim m As MQTTMSG = receivedObject
Dim msg1 As String = DecryptText(m.message)
Log("msg length = " & msg1.Length) ' logs 48
Log(msg1) ' logs, as per image below
End SubFor some reason, it is adding extra characters to the end of the message from what I can see.
Like I said, when I send it as plain text without encrypting the message it works fine.
Any ideas on what I have done wrong ?
