Hi all.
As promised is available library ProtectYourApp.
Just two minutes are required to implement the same within your apk.
Obviously I do not guarantee that it will never be unprotected, but definitely make life complicated for those who want to change your apk.
You can protect your APP and authorize, if you want, the same on some devices (this can be useful if you sell your license for a limited number of devices)
For more details Rel.2 look #3
ProtectYourApp
Author: Devil-App
Version: 2.00
You can see APK protect with this method here: DEMO HERE
If you want download and try
The library is not free. You need to donate as low as 15€ to get the library.
To send the money, just click on the Donate button below (the amount to enter is in euros).

As promised is available library ProtectYourApp.
Just two minutes are required to implement the same within your apk.
Obviously I do not guarantee that it will never be unprotected, but definitely make life complicated for those who want to change your apk.
You can protect your APP and authorize, if you want, the same on some devices (this can be useful if you sell your license for a limited number of devices)
For more details Rel.2 look #3
ProtectYourApp
Author: Devil-App
Version: 2.00
- ProApp
Methods:- IsInitialized As Boolean
Tests whether the object has been initialized. - cryptpya (text_crypt As String) As String
*This Crypt your string ( DB or Variable, etc. )
*Example:
Dim crypted1 As String = PYT.Cryptpya("Example Text crypto")
.....
Label1.Text = PYT.Decryptpya(crypted1) - decryptpya (text_crypt As String) As String
*This Decrypt your string ( DB or Variable, etc. )
*Example:
Dim crypted1 As String = PYT.Cryptpya("Example Text crypto")
.....
Label1.Text = PYT.Decryptpya(crypted1) - initialize As String
*This Initialize Library ProtectYourApp
*Example:
Dim PYT As ProApp
....
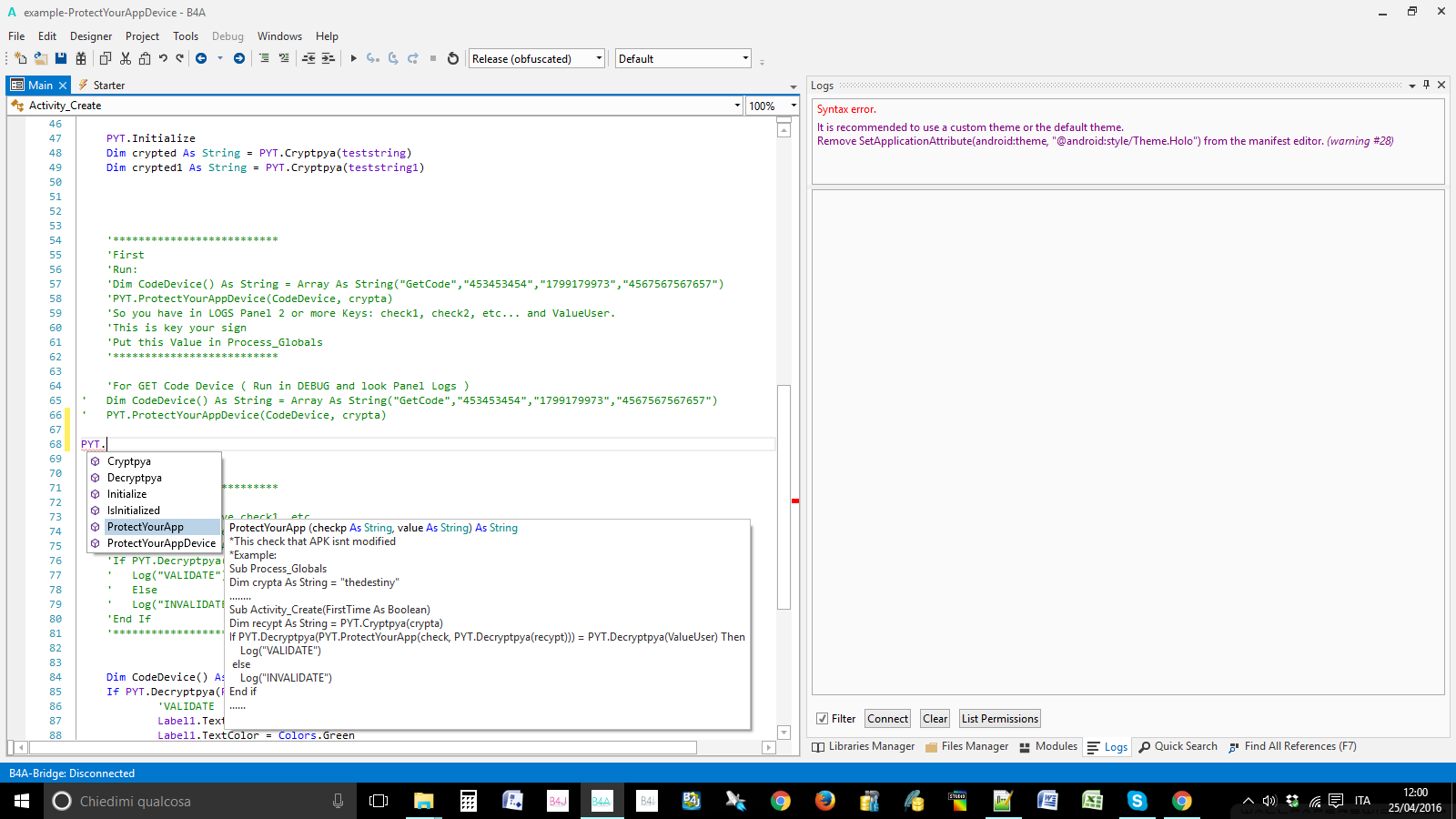
PYT.Initialize - Protectyourapp (checkp As String, value As String) As String
*This check that APK isnt modified
*Example:
Sub Process_Globals
Dim crypta As String = "thedestiny"
........
Sub Activity_Create(FirstTime As Boolean)
Dim recypt As String = PYT.Cryptpya(crypta)
If PYT.Decryptpya(PYT.ProtectYourApp(check, PYT.Decryptpya(recypt))) = PYT.Decryptpya(ValueUser) Then
Log("VALIDATE")
else
Log("INVALIDATE")
End if
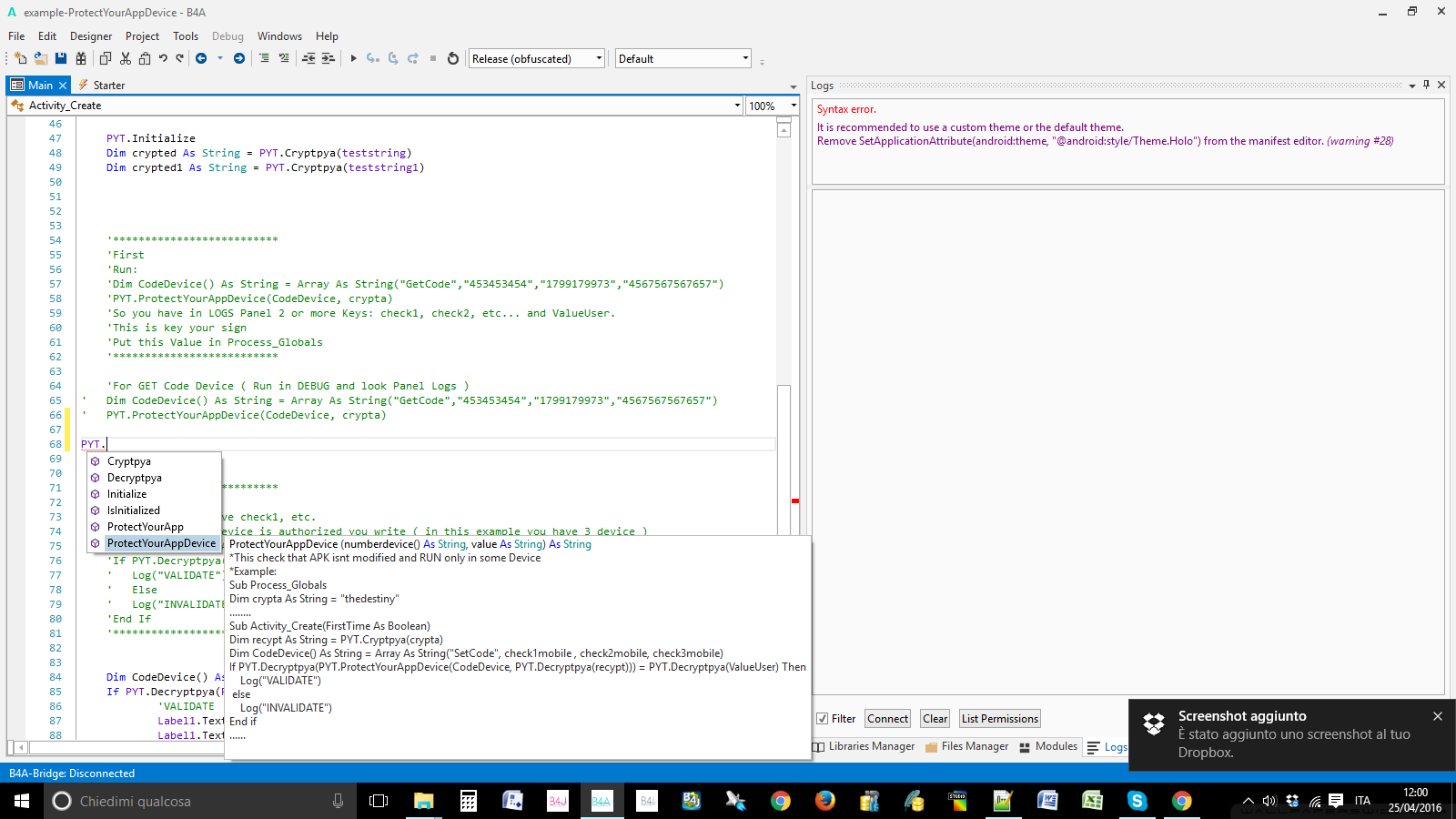
...... - Protectyourappdevice (numberdevice() As String, value As String) As String
*This check that APK isnt modified and RUN only in some Device
*Example:
Sub Process_Globals
Dim crypta As String = "thedestiny"
........
Sub Activity_Create(FirstTime As Boolean)
Dim recypt As String = PYT.Cryptpya(crypta)
Dim CodeDevice() As String = Array As String("SetCode", check1mobile , check2mobile, check3mobile)
If PYT.Decryptpya(PYT.ProtectYourAppDevice(CodeDevice, PYT.Decryptpya(recypt))) = PYT.Decryptpya(ValueUser) Then
Log("VALIDATE")
else
Log("INVALIDATE")
End if
......
- IsInitialized As Boolean
You can see APK protect with this method here: DEMO HERE
If you want download and try
The library is not free. You need to donate as low as 15€ to get the library.
To send the money, just click on the Donate button below (the amount to enter is in euros).

Last edited:
