This is a continuation of: https://www.b4x.com/android/forum/t...-as-virus-false-positives.147513/#post-935210
The Problem
Consequences:
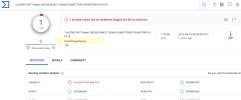
1. Check: External Scan of apk
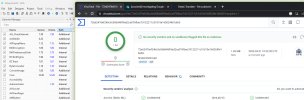
A check using virustotal.com gives 2 hits and 63 ok:
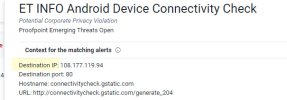
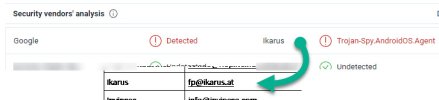
Icarus classifies it as "Trojan-Spy.AndroidOS.Agent"
2. Check: Removal of libs and renewed external scan
With the help of @MarcoRome (see previous thread) some libs were looked at more closely and disabled individually.
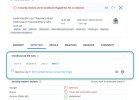
3. Check:
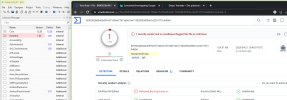
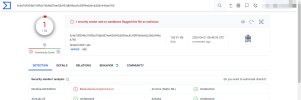
A new neutral default app (see "falsepostest1.zip") was scanned with the following result:
1 hit and 64 ok:
4. Further, planned procedure
b) Create an empty default app with all libs and modules of the source file.
The Problem
Apk files that are uploaded to Google Drive are marked there as virus infected.
Consequences:
- The affected files can then no longer be shared via a share link.
- The affected files can then no longer be uploaded to Play Store
- Economic loss, as the product can no longer be marketed
1. Check: External Scan of apk
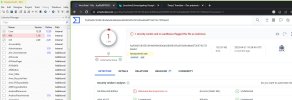
A check using virustotal.com gives 2 hits and 63 ok:

The effect occurs with obfuscated and without obfuscation.
2. Check: Removal of libs and renewed external scan
With the help of @MarcoRome (see previous thread) some libs were looked at more closely and disabled individually.
The result of the scans was unchanged.
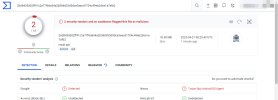
3. Check:
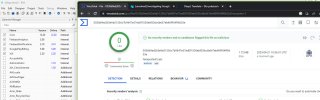
A new neutral default app (see "falsepostest1.zip") was scanned with the following result:
1 hit and 64 ok:

McAfee-GW-Edition classifies it as "BehavesLike.Suspicious.cc"
This result is different, but interesting.
4. Further, planned procedure
a) Create an empty default app with all libs of the source file
If anyone has experience with this problem or can make concrete usable suggestions, input would be appreciated.Attachments
Last edited: